Secure Service Edge (SSE)
Enabling the future of work, redefining risk management & simplifying operations.

The Challanges.
Supporting business growth and the dynamic nature of remote work.
FUTURE-PROOFING THE ORGANIZATION
Keep up with the evolving cyber threats and digital transformation
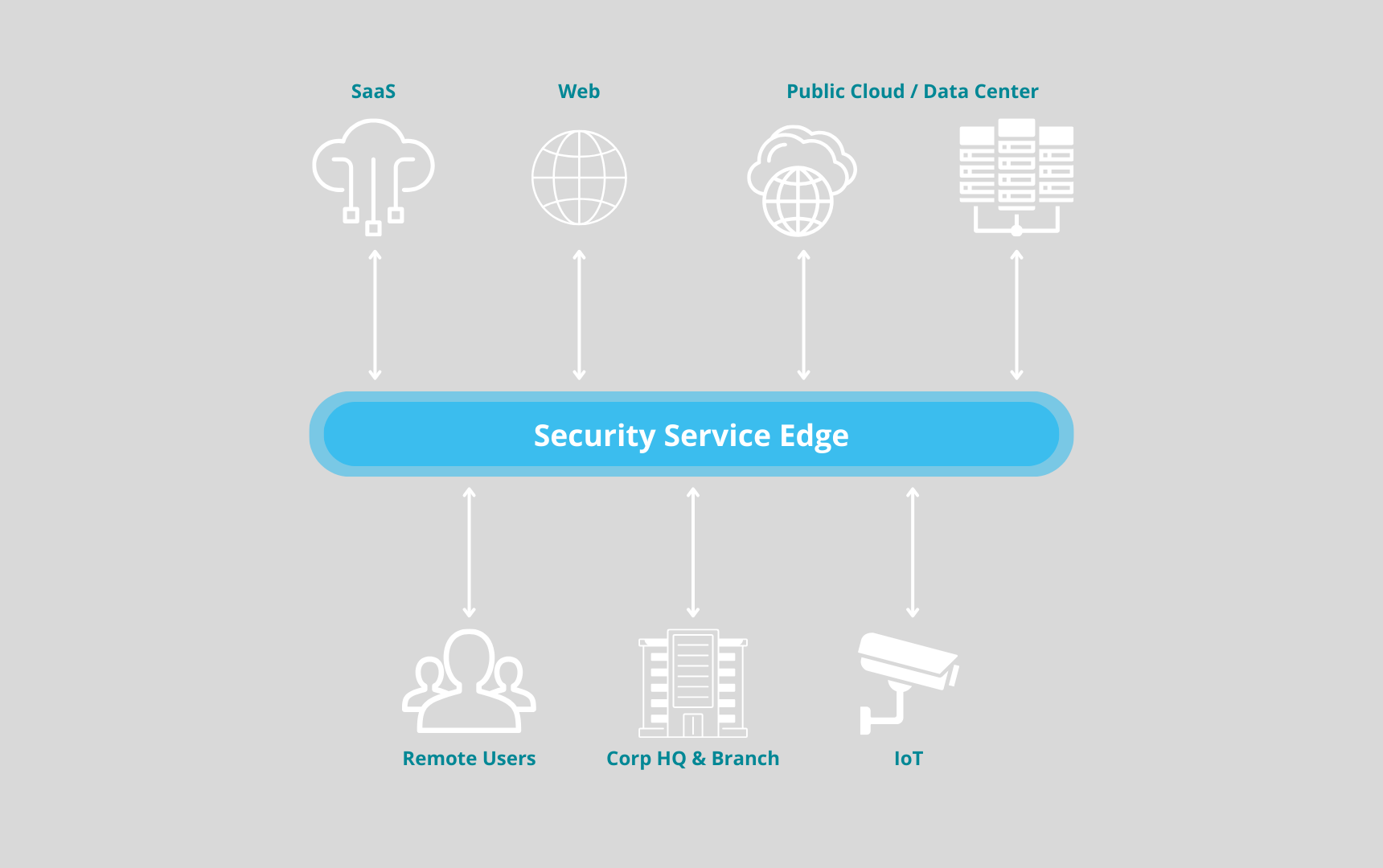
Implementing a Security Service Edge (SSE) solutions addresses critical challenges in today’s digital-first business environment, where traditional security models fall short.
SSE provides a modern, consolidated approach to security that enhances protection, ensures compliance, improves performance, and reduces costs, all while offering scalability and future-proofing the organization.
SIMPLIFYING OPERATIONS
Enabling the future of work
Security Service Ege (SSE) enables the future of work, redefines risk management and data protection, and simplifies operations – a new security fabric
Consolidation of, VPN, SaaS, and Secure Internet traffic – saves time and money and increases the Cybersecurity level.
Many disparate policies become one.
Coverage for any user, any location, any app, any data movement.
Zero Trust enabler
Customer value.
Guiding customers through the journey from assessment to implementation.
Sciber's structured, hands-on approach ensures that the customer not only selects the most fitting SSE solution but also benefits from its effective deployment and ongoing management, aligning with their security requirements and business goals.
Identify Needs
Sciber starts by understanding the customer's current cybersecurity posture, identifying specific needs, and objectives. This involves a comprehensive evaluation of the customer’s network architecture, applications, data flows, and remote access requirements.
Vendor evaluation
Market research
Future comparison
Proof of concept
Training and enablement
Staff training
Documentation
Support an optimization
Monitoring and support
Periodic Reviews